15+ Preimage Calculator
If a function f is such that fx a the preimage of a by the function f. Preimage of a Function Equation Solver.
The Old Reader
It is denoted as.
. A map fXY is proper if the preimage under f of any question_answer Q. Printcopy and complete the 915 HW. - Verification of an ECDSA signature under specific parameters - Preimage of a hash function output Post.
The preimage is dilated by a scale factor of n. Meaning of image and preimage. R ab.
Entity Post-Image Pre-Image preimage and post image Read Workflow Post navigation Business Rule Updates in Dynamics CRM 2015 Part II Extending Sharepoint 2013 and integrating with CRM 2013 IFD. The codomain is the set of all possible values which can come out as a result but the range is the set of values which actually comes out. Use the distance formula to help you decide.
As an example consider the real-valued function. If a shape is transformed its appearance is changed. Please let us know if you have questions or need clarificationThe 915 HW assignment and key will be posted as tomorrows assignment.
This is the best place to expand your knowledge and get prepared for your next interview. LeetCode Online Judge is a website containing many algorithm questionsMost of them are real interview questions of Google Facebook LinkedIn Apple etc. Bitcoin has been designed to only check two conditions.
This repository includes my solutions to all Leetcode algorithm questions. The term one-to-one correspondence should not be confused with the one-to-one function ie injective function. 226 invert binary tree.
Thus every element in the codomain has a preimage in the domain. Preimage Size of Factorial Zeroes Function. 241 Some functions and their graphs.
It sends each element to the unique element such that fx y. Hence it is an example of a function. For a function its inverse.
225 implement stack using queues. This problems mostly consist of real interview questions that are asked on big companies like Facebook Amazon Netflix Google etc. B is called the image of a under f and a is called the preimage of b under f.
Enc K D HashK and ZK proof that the hashed key what is sophos ips A hybrid smart contract is an application that consists of two parts. Historically it was widely used as a cryptographic hash. Packer conditional provisioner votes Vote Now.
Therefore by the definition of onto g is onto. Wednesday March 25th 915 Assignment Step One. Admits an explicit description.
The slope of the corresponding line segment in the image is m nm. 227 basic calculator ii. MD5 was designed by Ronald Rivest in 1991 to replace an earlier hash function MD4 and was specified in 1992 as RFC 1321.
The difference between codomain and range is a bit difficult to find out because both the terms sometimes means the same. The actual meaning of transformations is a change of appearance of something. Image Set Calculator.
What is the difference between image and preimage. 序 关于 LeetCode 说到 LeetCode作为一个程序员来说应该不陌生近几年参加面试都会提到它国内外的程序员用它刷题主要是为了面试据历史记载这个网站 2011 年就成立了马上就要到自己 10 周年的生日了每周举行周赛双周赛月赛在有限时间内编码确实非常能考验人的算法能力. Any cryptographic hash function such as SHA-2 or SHA-3 may be used in the calculation of an HMAC.
Leetcode Python solutions About. Enter the amount in Amount field. Ba 2 ab N.
In mathematics the inverse function of a function f also called the inverse of f is a function that undoes the operation of fThe inverse of f exists if and only if f is bijective and if it exists is denoted by. The resulting MAC algorithm is termed HMAC-X where X is the hash function used eg. Choose the crypto from the search list.
Simply select the currency pair you are trading enter your account currency and your position. N be the set of Natural numbers and the relation R be defined as. So given an arbitrary element of the codomain we have shown a preimage in the domain.
But still we can slightly differentiate between range and codomain. The Range is found after substituting the possible x- values to find the y-values. The domain is defined as the entire set of values possible for independent variables.
Free digital tools for class activities graphing geometry collaborative whiteboard and more. And it always help to sharp our algorithm SkillsLevel up your coding skills and quickly land a job. The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value.
1 5 9 11 15 16. Letter Combinations of a Phone Number. Check your answers using the 915 HW Key.
You can use Crypto Coverter Calculator tool to convert cryptocurrency to fiat or crypto to cryptoStep 1. Remove Nth Node From End of List. If you need to please reference the videonotes posted yesterday.
After that the shape could be congruent or similar to its preimage. MD5 can be used as a checksum to verify data integrity against unintentional corruption. If f is the function from X to Y and xy f then fx y where y is the image of x under function f and x is the preimage of y under f.
1 smart contract code that runs. Dynamics CRM Dynamics CRM 2013 Dynamics CRM 2015 Dynamics CRM 2016 Workflows Tags. In this article we are going to discuss the definition of the bijective function with examples and let us learn how to prove that the given function is.
Function f Variable Search image for value Calculate. Making A Large Island. Choose the option convert from crypto to fiat or crypto to cryptoStep 2.
Find the domain and range of a function fx 3x 2 5. HMAC-SHA256 or HMAC-SHA3-512The cryptographic strength of the HMAC depends upon the cryptographic strength of the underlying hash function the size of its hash. State whether R is a relation function or not.
The geometric transformation is a bijection of a set that has a geometric structure by itself or another set. M 6 AB 35 37. In probability theory and statistics the exponential distribution is the probability distribution of the time between events in a Poisson point process ie a process in which events occur continuously and independently at a constant average rateIt is a particular case of the gamma distributionIt is the continuous analogue of the geometric distribution and it has the key.
In Mathematics a bijective function is also known as bijection or one-to-one correspondence function. The length of the corresponding line segment in the image is x nx units. It gains uniqueness from the big stuffed head that comes in bulb shape.
Modeling jobs for 15 year olds Free Crochet Octopus Pattern This uniquely crocheted octopus preemie stuffed toy is 27cm tall. The height of a person can be determined by the length of his femur bone. After adding a markup of 20 on the cost of an item a shop keeper sold the item for K336.
A preimage includes a line segment with a length of x units and a slope of m units.

What Is A Preimage Attack And Are They Dangerous
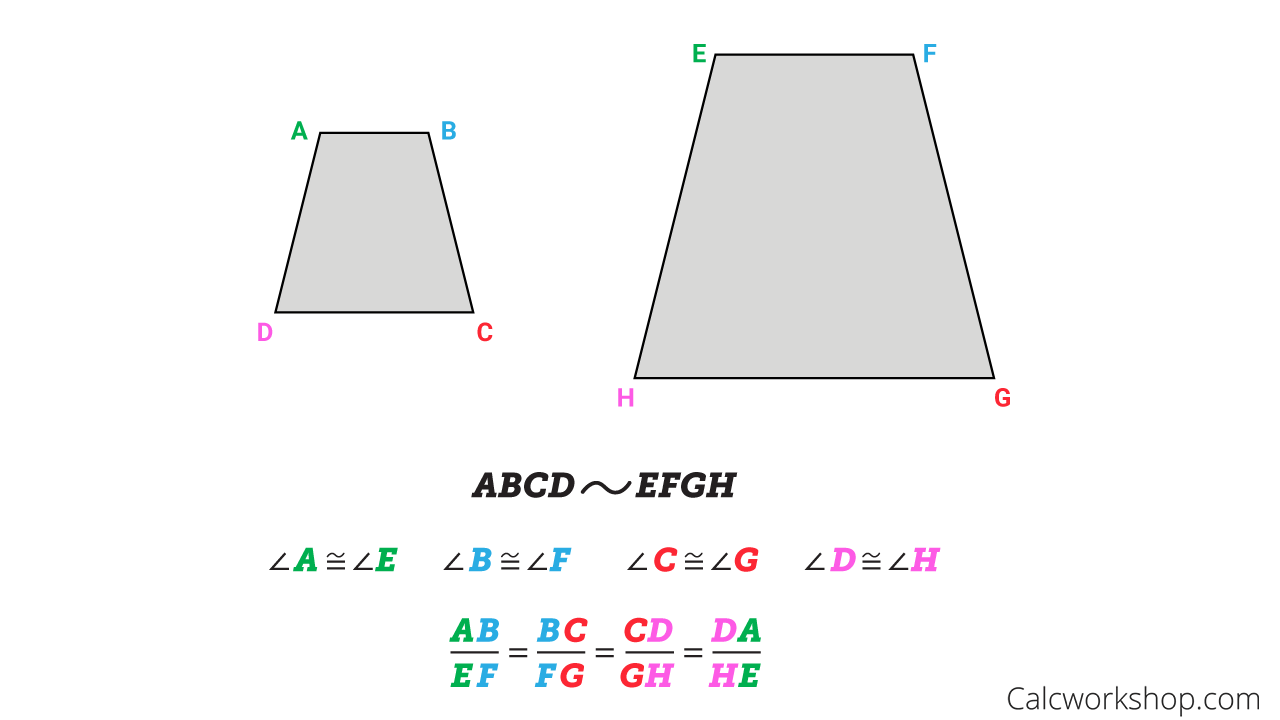
Similar Polygons Explained W 23 Step By Step Examples

Transformations In Math Definition Types Examples Video

A Point A Is Reflected Over The Mirror Line B The Pre Image Point Download Scientific Diagram
Ixl Rotations

Discrete Math Preimage Functions R Homeworkhelp
Ixl Dilations

E Preimage Of Two Dsls With Chain Code 0101 And 0100 The Union Download Scientific Diagram
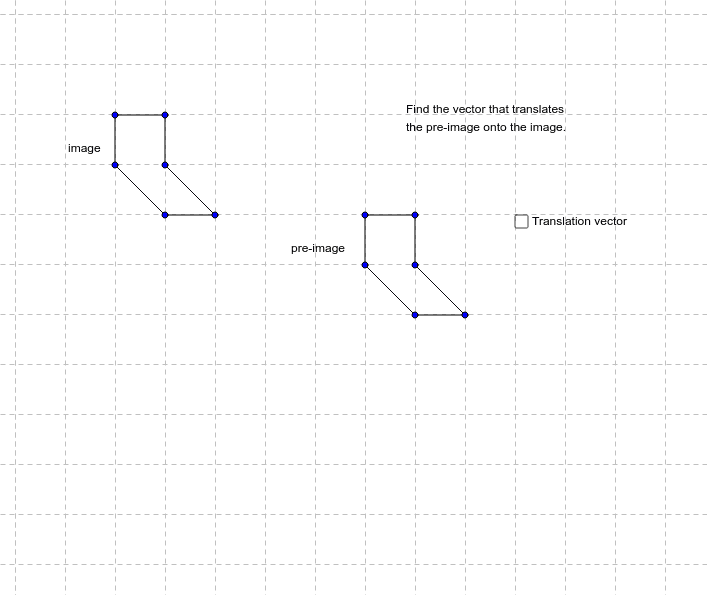
Translation Vector From Given Pre Image And Image Geogebra
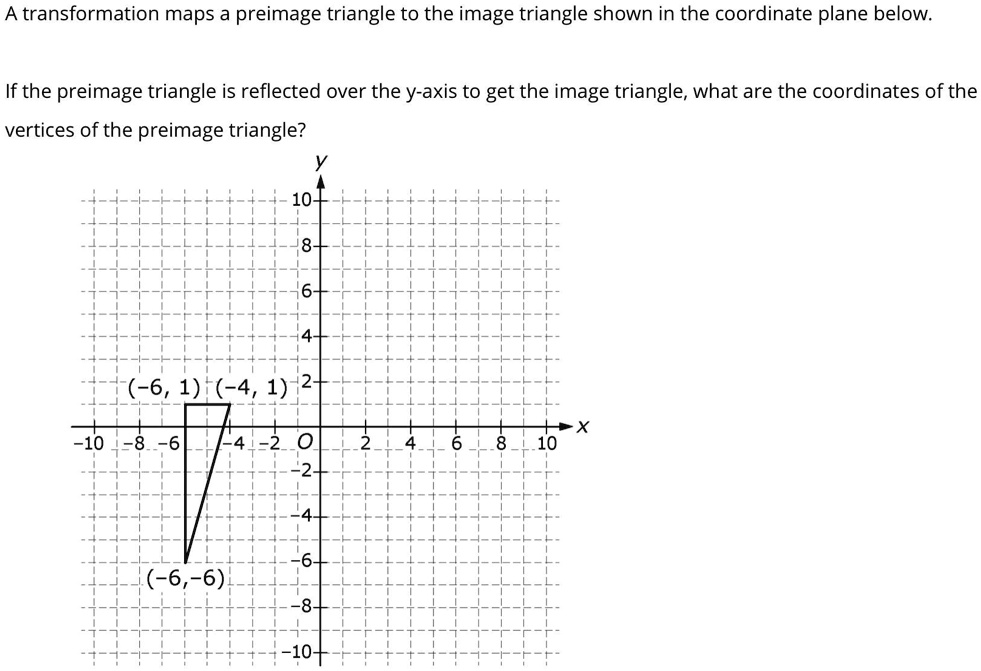
Solved Please Help Look At The Image Answer Choices Look At The Next Image A Transformation Maps A Preimage Triangle To The Image Triangle Shown In The Coordinate Plane Below If The
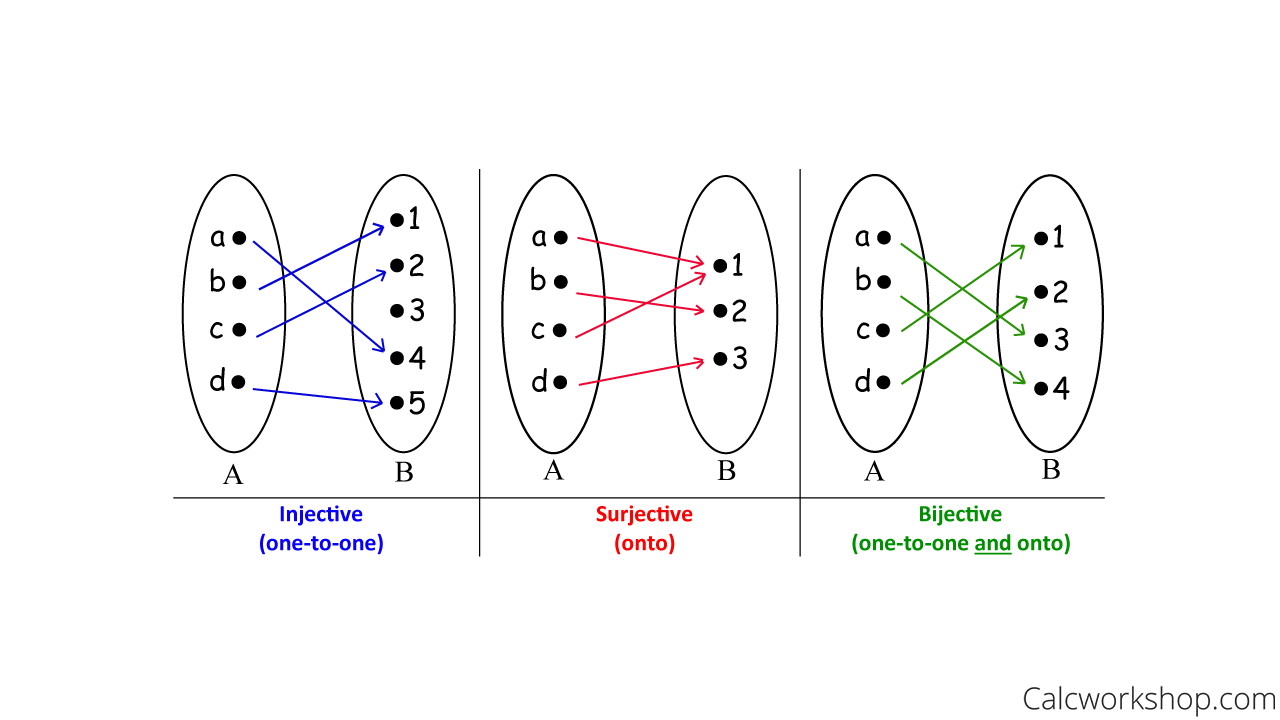
Bijection How To Prove W 9 Step By Step Examples

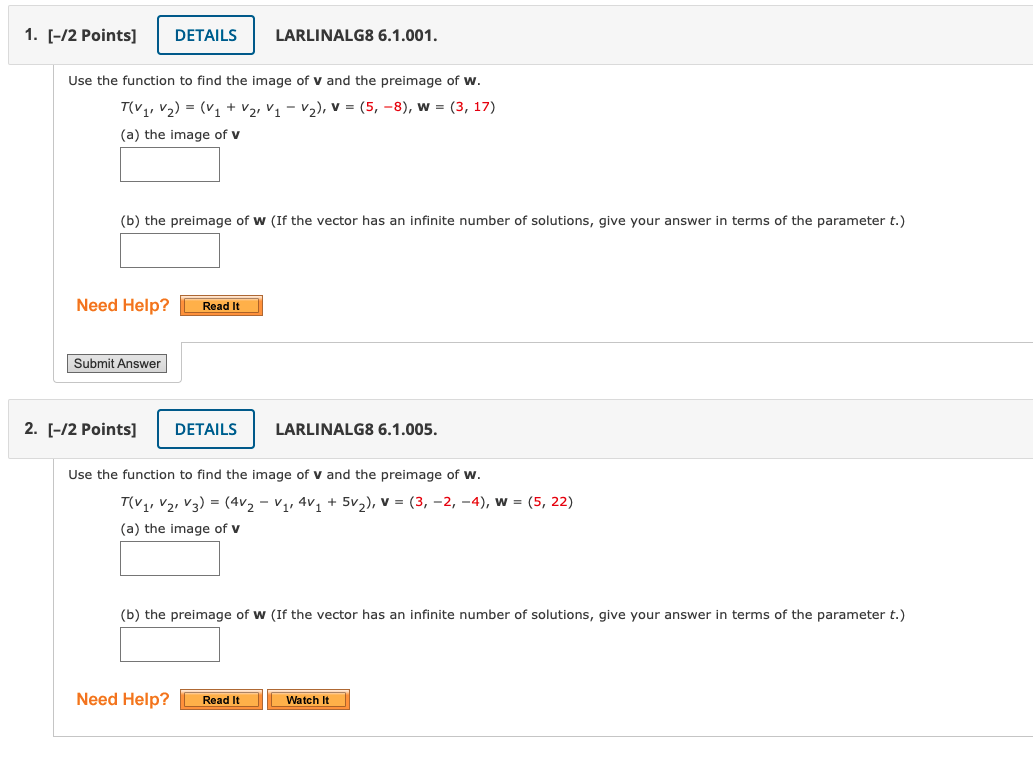
Solved Use The Function T V1 V2 V3 2v V2 11 12 Chegg Com

The Preimage And The Image After A Translation Coincide What Can You Say About The Translation
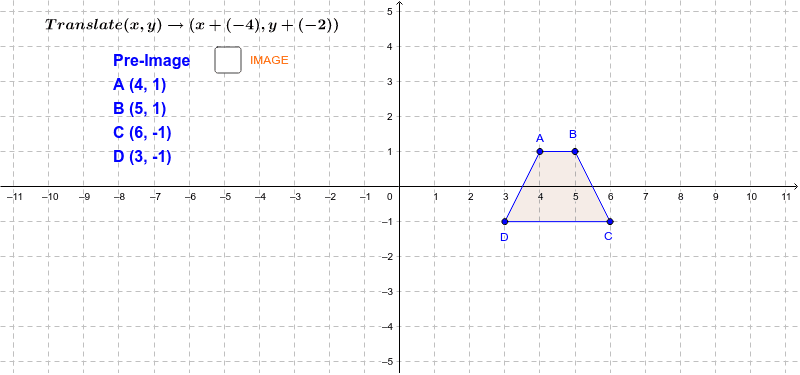
Translation Geogebra
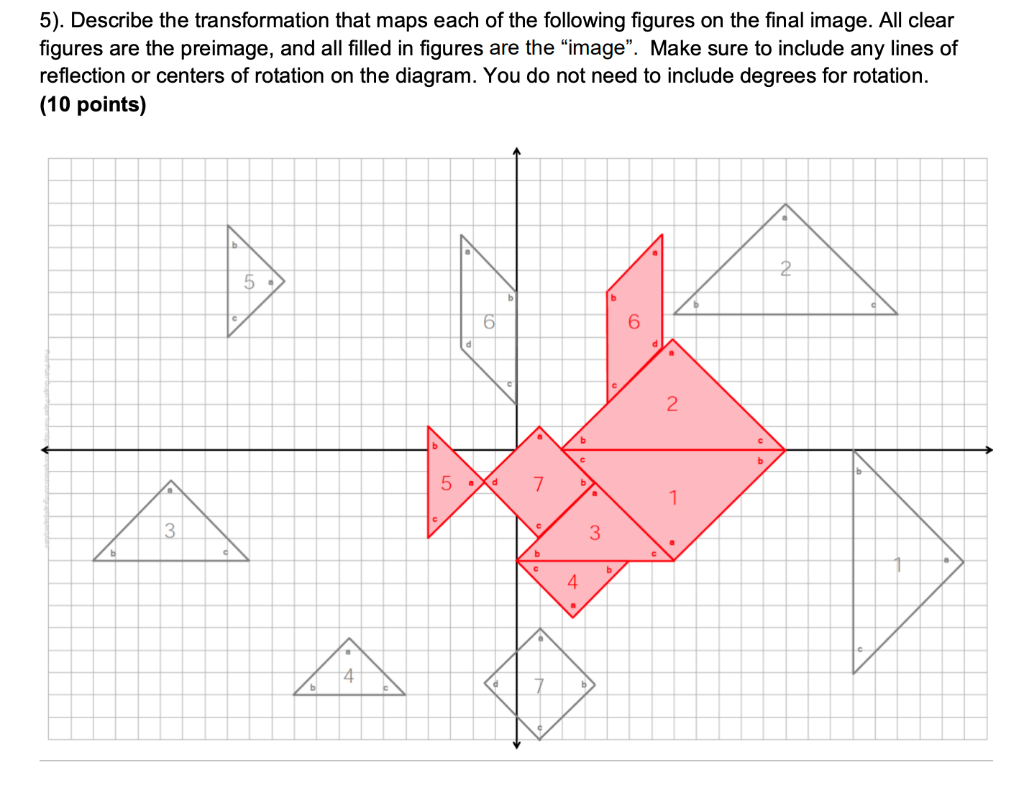
Solved 5 Describe The Transformation That Maps Each Of The Chegg Com

The Old Reader
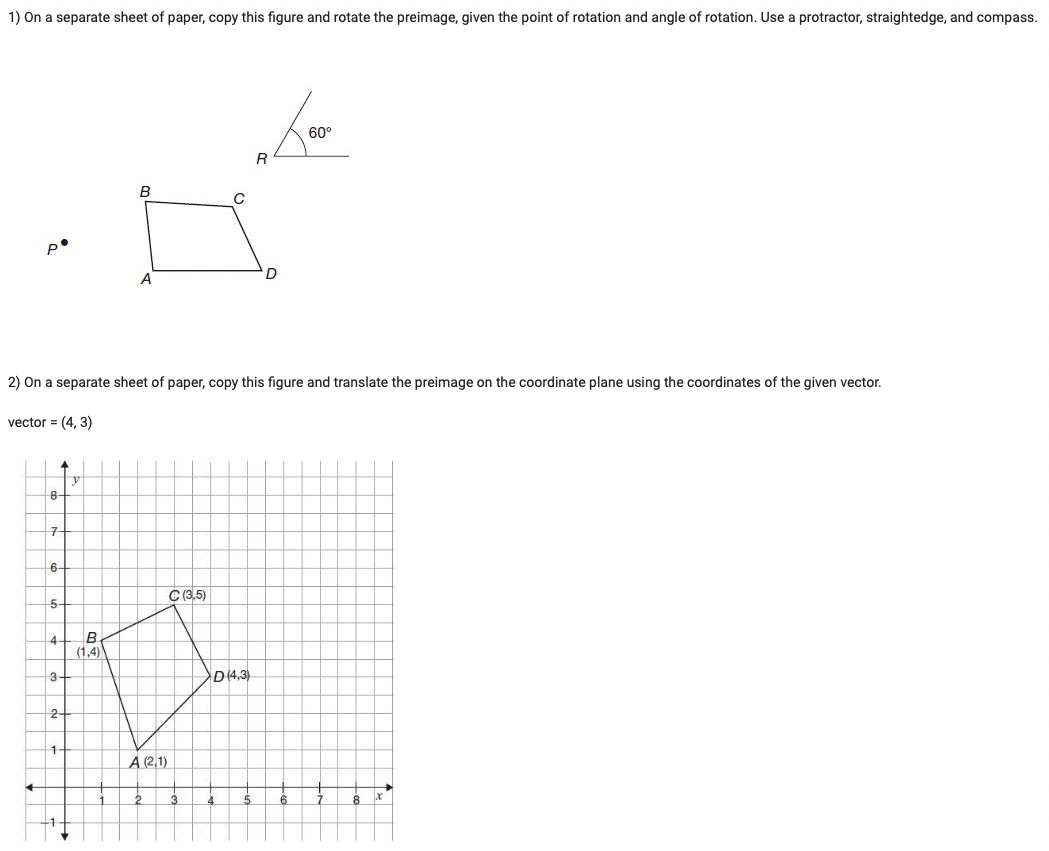
Answered 1 On A Separate Sheet Of Paper Copy Bartleby